| 241. | Microsoft throws spox under the bus in ICC email flap | (theregister.com) |
|
|
||
| 3 points by abdelhousni 23 hours ago | 0 comments |
| 242. | What Every Experimenter Must Know About Randomization | (spawn-queue.acm.org) |
|
|
||
| 7 points by underscoreF 4 days ago | 0 comments |
| 243. | EU mandates replaceable batteries by 2027 (2023) | (environment.ec.europa.eu) |

|
The new law will ensure that batteries are collected, reused and recycled in Europe and will support the shift to a circular economy. | |
| 8 points by cyrusmg 1 day ago | 2 comments |
| 244. | Attention is all you need to bankrupt a university | (hollisrobbinsanecdotal.substack.com) |
|
Unbalancing the books | |
| 4 points by HR01 1 day ago | 0 comments |
| 245. | SE Radio 708: Jens Gustedt on C in 2026 | (se-radio.net) |
|
|
||
| 3 points by matt_d 3 days ago | 0 comments |
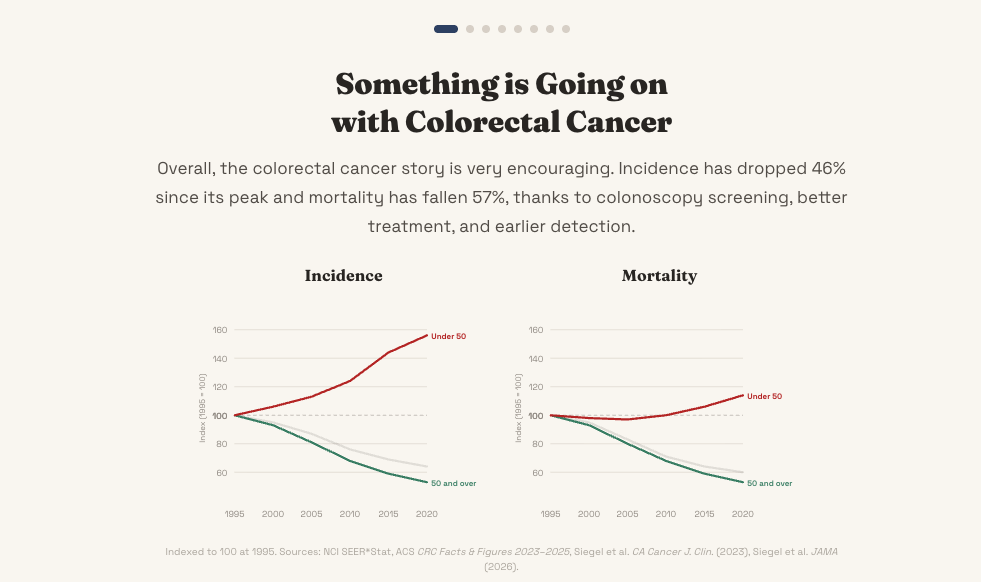
| 246. | Overall, the colorectal cancer story is encouraging | (hankgreen.com) |
|
An interactive data journalism piece exploring the rise of young-onset colorectal cancer, with population simulations, risk factors, and prevention information. | |
| 39 points by ZeroGravitas 3 days ago | 21 comments |
| 247. | Against Theory-Motivated Experimentation | (journals.sagepub.com) |
|
|
||
| 4 points by paraschopra 3 days ago | 1 comments |
| 248. | AI Makes You Boring | (marginalia.nu) |
|
|
content | |
| 139 points by speckx 3 days ago | 74 comments |
| 249. | Netbase: A port of the NetBSD utilities for Linux | (github.com) |
|
|
A port of the netbsd utilities for linux(and may be another unix like operating systems) - littlefly365/Netbase | |
| 3 points by jaypatelani 3 days ago | 0 comments |
| 250. | Show HN: CEL by Example | (celbyexample.com) |
|
|
Common Expression Language Examples | |
| 5 points by bufbuild 4 days ago | 0 comments |
| 251. | Surreal Number | (en.wikipedia.org) |

|
||
| 3 points by the-mitr 15 hours ago | 0 comments |
| 252. | Minecraft Java is switching from OpenGL to Vulkan | (gamingonlinux.com) |
|
|
Work continues for the Vibrant Visuals update to come to Minecraft Java, and as part of that they're switching the rendering from OpenGL to Vulkan. | |
| 19 points by tuananh 4 days ago | 1 comments |
| 253. | Poland bans camera-packing cars made in China from military bases | (theregister.com) |
|
|
||
| 5 points by Bender 13 hours ago | 0 comments |
| 254. | IPv6 Adoption in 2026 | (netmeister.org) |

|
||
| 4 points by zdw 3 days ago | 0 comments |
| 255. | Show HN: A Lisp where each function call runs a Docker container | (github.com) |
|
|
A Docker image is a piece of executable code that produces some output given some input. - a11ce/docker-lisp | |
| 7 points by a11ce 4 days ago | 2 comments |
| 256. | I traced 3,177 API calls to see what 4 AI coding tools put in the context window | (theredbeard.io) |

|
Claude used 23K tokens to fix a one-line bug. Gemini used 350K. I built a tool to find out why. | |
| 4 points by theredbeard 3 days ago | 0 comments |
| 257. | Graphs are maximally expressive for higher-order interactions | (arxiv.org) |
|
|
||
| 4 points by E-Reverance 1 day ago | 0 comments |
| 258. | Testing Super Mario Using a Behavior Model Autonomously | (testflows.com) |
|
|
An article about autonomous testing of Super Mario using behavior models and evolutionary state space exploration techniques. | |
| 7 points by Naulius 2 days ago | 1 comments |
| 259. | Ask HN: Do US presidents have less fiduciary liability than CEOs? | () |
|
|
||
| 4 points by stopbulying 9 hours ago | 10 comments |
| 260. | Loon: A functional lang with invisible types, safe ownership, and alg. effects | (loonlang.com) |
|
|
Loon is a modern LISP with invisible types, algebraic effects, and ownership without annotations. | |
| 5 points by surprisetalk 2 days ago | 2 comments |
| 261. | Ask HN: Programmable Watches with WiFi? | () |
|
|
||
| 5 points by dakiol 1 day ago | 0 comments |
| 262. | From 'buy America' to 'bye America', Wall Street exodus gathers pace | (reuters.com) |
|
|
||
| 11 points by Bondi_Blue 2 days ago | 0 comments |
| 263. | Iranian Students Protest as Anger Grows | (wsj.com) |
|
|
||
| 6 points by JumpCrisscross 23 hours ago | 0 comments |
| 264. | Sam Altman Says Companies Are 'AI Washing' Layoffs | (gizmodo.com) |
|
|
Hold up, let him cook. | |
| 5 points by herbertl 8 hours ago | 0 comments |
| 265. | Judge scolds Zuckerberg's team for wearing Meta glasses to social media trial | (cbsnews.com) |

|
A Los Angeles judge ordered Meta officials to remove their AI glasses at a trial over the impact of social media on users. | |
| 8 points by ColinWright 2 days ago | 0 comments |
| 266. | Microsoft offers guide to pirating Harry Potter series for LLM training | (devblogs.microsoft.com) |
|
|
||
| 18 points by anonymous908213 4 days ago | 3 comments |
| 267. | A psychedelic medicine performs well against depression | (economist.com) |
|
|
||
| 4 points by vinni2 3 days ago | 1 comments |
| 268. | Escaping flatland: career advice for CS undergrads | (space.ong.ac) |
|
|
tl;dr: a message to myself, and to incoming CS undergrads. even if impostor syndrome hits hard, you’re all smart and competent people. and you’re now smart and competent enough that everyone wants a piece of your potential. | |
| 4 points by jxmorris12 3 days ago | 0 comments |
| 269. | Discrete Structures [pdf] | (kyleormsby.github.io) |
|
|
||
| 8 points by mathgenius 4 days ago | 1 comments |
| 270. | Escaping Misconfigured VSCode Extensions (2023) | (blog.trailofbits.com) |
|
|
TL;DR: This two-part blog series will cover how I found and disclosed three vulnerabilities in VSCode extensions and one vulnerability in VSCode itself (a security mitigation bypass assigned CVE-2022-41042 and awarded a $7,500 bounty). We will identify the underlying cause of each vulnerability and create fully working exploits to demonstrate how an […] | |
| 4 points by abelanger 2 days ago | 0 comments |