| 151. | Pi for Excel: AI sidebar add-in for Excel, powered by Pi | (github.com) |
|
|
Experimental Excel sidebar agent add-in. Multi-model. Powered by Pi. - tmustier/pi-for-excel | |
| 8 points by rahimnathwani 3 days ago | 0 comments |
| 152. | Unsung heroes: Flickr's URLs scheme | (unsung.aresluna.org) |
|
A blog about software craft and quality | |
| 3 points by onli 1 day ago | 0 comments |
| 153. | Archaeologists find possible first direct evidence of Hannibal's war elephants | (smithsonianmag.com) |
|
|
The Carthaginian general famously used elephants during the Punic Wars. But until now, archaeologists had never found skeletal remains linking the animals to the conflict | |
| 6 points by bryanrasmussen 3 days ago | 1 comments |
| 154. | The Popper Principle | (theamericanscholar.org) |
|
|
||
| 3 points by lermontov 3 days ago | 0 comments |
| 155. | Untapped Way to Learn a Codebase: Build a Visualizer | (jimmyhmiller.com) |
|
|
||
| 3 points by andreabergia 2 days ago | 0 comments |
| 156. | I'm #1 on Google thanks to AI bullshit [video] | (youtube.com) |

|
my original video: https://youtu.be/II2QF9JwtLcandy's videos: GOOD WATCH:https://youtu.be/Vk8x0iRr2ekhttps://youtu.be/RJfWi5qRuAc | |
| 4 points by basilikum 1 day ago | 0 comments |
| 157. | Measuring AI agent autonomy in practice | (anthropic.com) |
|
|
Anthropic is an AI safety and research company that's working to build reliable, interpretable, and steerable AI systems. | |
| 5 points by jbredeche 3 days ago | 2 comments |
| 158. | Fast KV Compaction via Attention Matching | (arxiv.org) |
|
|
Abstract page for arXiv paper 2602.16284: Fast KV Compaction via Attention Matching | |
| 3 points by cbracketdash 2 days ago | 0 comments |
| 159. | It's impossible for Rust to have sane HKT | (vspefs.substack.com) |

|
We know that Rust reifies regions as types. | |
| 3 points by emschwartz 8 hours ago | 0 comments |
| 160. | AOMedia Open Audio Codec 'OAC' Aims to Be the Successor to Opus | (phoronix.com) |
|
|
While the Alliance For Open Media 'AOMedia' is most known for developing the AV1 open video codec, the associated AV1 Image File Format (AVIF), and the next-generation AV2, they are now working on the Open Audio Codec (OAC). | |
| 3 points by snowhale 10 hours ago | 0 comments |
| 161. | Ace is a complete BASIC compiler for the Amiga computer platform | (github.com) |
|
|
AmigaBasic ACE. Contribute to mdbergmann/ACEBasic development by creating an account on GitHub. | |
| 3 points by doener 1 day ago | 0 comments |
| 162. | Show HN: An encrypted, local, cross-platform journaling app | (github.com) |
|
|
A local-first journal with serious encryption. Free, open source, and never touches the internet. - fjrevoredo/mini-diarium | |
| 7 points by holyknight 3 days ago | 0 comments |
| 163. | Web Components: The Framework-Free Renaissance | (caimito.net) |

|
Modern browsers now support everything needed to build sophisticated, reactive web interfaces without React, Vue, or Angular. Web components, custom elements, shadow DOM, and native event systems l... | |
| 5 points by mpweiher 2 days ago | 1 comments |
| 164. | Iran students stage first large anti-government protests since deadly crackdown | (bbc.com) |

|
Student protesters honoured thousands of those killed when nationwide mass protests were put down by Iranian authorities last month. | |
| 27 points by tartoran 14 hours ago | 6 comments |
| 165. | Anthropic officially bans using subscription auth for third party use | (code.claude.com) |
|
|
Legal agreements, compliance certifications, and security information for Claude Code. | |
| 8 points by theahura 4 days ago | 1 comments |
| 166. | Fedify 2.0.0: Modular architecture, debug dashboard, and relay support | (github.com) |
|
|
Fedify 2.0.0: Modular architecture, debug dashboard, and relay support | |
| 5 points by dahlia 16 hours ago | 0 comments |
| 167. | Old School Visual Effects: The Cloud Tank (2010) | (singlemindedmovieblog.blogspot.com) |

|
||
| 3 points by exvi 3 days ago | 0 comments |
| 168. | Red Robin Died by Spreadsheet. Don't Make the Same Mistake | (garryslist.org) |

|
||
| 5 points by mooreds 1 day ago | 0 comments |
| 169. | Dinosaur Food: 100M year old foods we still eat today | (borischerny.com) |
|
|
I just finished Oliver Sacks’ excellent Everything in Its Place. In it, he mentioned as an aside that the Ginkgo biloba tree is hundreds of millions of years old, and its phenotype has been practically frozen since then – a living fossil. | |
| 8 points by simonebrunozzi 3 days ago | 0 comments |
| 170. | Consistency diffusion language models: Up to 14x faster, no quality loss | (together.ai) |
|
Standard diffusion language models can't use KV caching and need too many refinement steps to be practical. CDLM fixes both with a post-training recipe that enables exact block-wise KV caching and trajectory-consistent step reduction — delivering up to 14.5x latency improvements | |
| 9 points by zagwdt 2 days ago | 1 comments |
| 171. | America vs. Singapore: You Can't Save Your Way Out of Economic Shocks | (governance.fyi) |

|
Saving regret has less to do with procrastination than we thought, and more to do with whether your country absorbs economic shocks or lets them hit your savings | |
| 6 points by guardianbob 3 days ago | 0 comments |
| 172. | Paged Out Issue #8 [pdf] | (pagedout.institute) |
|
|
||
| 22 points by SteveHawk27 3 days ago | 4 comments |
| 173. | Explaining Why NASA's Starliner Report Is So Bad | (youtube.com) |

|
I took a couple of days to read NASA's Starliner Reportand figure out as much of the technical detail as possible, there are a lot of redactions that require... | |
| 5 points by Betelbuddy 9 hours ago | 0 comments |
| 174. | 27-year-old Apple iBooks can connect to Wi-Fi and download official updates | (old.reddit.com) |
|
|
||
| 9 points by surprisetalk 4 days ago | 0 comments |
| 175. | Show HN: Ghostty and Watercolors | (jrmeyer.github.io) |
|
|
||
| 5 points by _josh_meyer_ 1 day ago | 1 comments |
| 176. | Mathematics in the Library of Babel | (daniellitt.com) |

|
Mathematics isn't only about saying true things. It's about asking the right questions, being confused, stumbling about, getting distracted, being wrong, recognizing when you're wrong, being stuck. Mostly being stuck. It's about clinging to a giant edifice and feeling it out until you understand some tiny piece of it. It's about finding meaning in and intuition for the texture of an object which, at first, can only be apprehended by bashing your skull into it until it imprints on your forehead. Then trying to convey some of that insight to someone else, and watching as they find their own way to it. I started trying to get LLMs to do math in July 2020, through the game "AI Dungeon," one of the earliest applications powered by GPT-3. I first got GPT-3 to produce a correct proof (of Fermat's Little Theorem) in April 2022. At the time I did not think they would become useful for math research in the near term. This changed when the first reasoning models were released: on February 1, 2025, I wrote that the model o3-mini-high “clearly has passed the threshold of genuine usefulness” for research, while still making many, many mistakes. Since then, the models have improved, and ChatGPT 5.2 Pro (released in December 2025) can regularly provide reasonable proofs of lemmas that I would characterize as “involved but routine for experts,” though it still makes many errors. And I have been using Codex, OpenAI's coding/computer use agent, for scientific computing tasks I would not have considered attempting a few months ago. In public comments, I've tried to credit successes while pushing back against hype. I've talked a lot about "slop" papers on arXiv. I have worried that we are polluting the scientific commons with incorrect mathematics whose errors are enormously difficult to detect. I've tried to focus on the present. In this essay I'll talk about the future. | |
| 3 points by robinhouston 1 day ago | 0 comments |
| 177. | Bridging Elixir and Python with Oban | (oban.pro) |

|
Using Oban to seamlessly exchange durable jobs between Elixir and Python applications through a shared PostgreSQL database. | |
| 4 points by sorentwo 3 days ago | 0 comments |
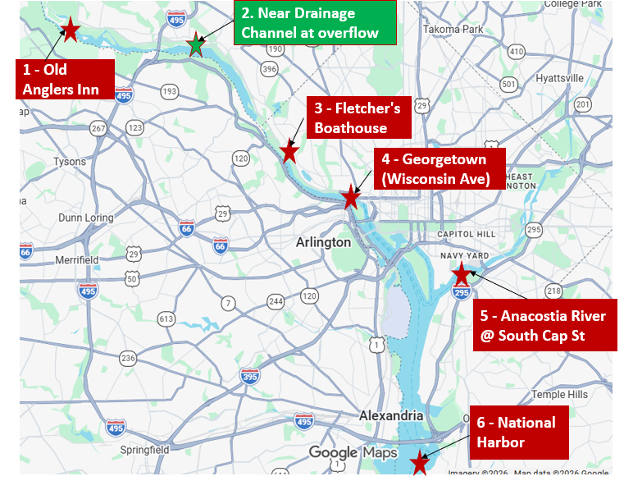
| 178. | Sewage Spill in the Potomac River | (vdh.virginia.gov) |
|
||
| 3 points by geox 15 hours ago | 0 comments |
| 179. | Toggle: A simple and keyboard friendly graphics drawing tool | (github.com) |
|
|
Simple and keyboard-driven graphics drawing tool. Contribute to Protyasha-Roy/toggle development by creating an account on GitHub. | |
| 3 points by zynovex 1 day ago | 0 comments |
| 180. | ATAboy is a USB adapter for legacy CHS only style IDE (PATA) drives | (github.com) |
|
|
ATAboy is a user-friendly bridge that allows legacy CHS only style IDE (PATA) hard drives to be connected to a modern computer as a standard USB Mass Storage device. - redruM0381/ATAboy | |
| 6 points by zdw 2 days ago | 0 comments |